If there's one thing we all need to be on guard about these days, it's data breaches. And if you think, 'I don't need to worry about those; I have a super-secret password!' Well, you could be right, but you could also be wrong. I'm going to use the word 'hacker' loosely here, but the complexity of your password becomes irrelevant if your credentials were compromised in a data breach. Hackers can get their hands on your personal info without you even knowing it, simply by buying them online after a data breach.
I've been through a data breach myself, and today, while helping a coworker deal with compromised credentials, it got me thinking about the importance of knowing what to do when you find out you're part of one. That's where this article comes in. I want to walk you through the steps to take when you suspect your data might have been compromised and how to figure out which of your email addresses and credentials got caught up in the mess. Once we've figured that part out, let's break down what you can do to mitigate the problem and how to prevent any unauthorized access to your accounts.
Understanding Data Breaches
So, what's a data breach anyway? In plain English, it's when someone gets into a place they're not supposed to be and grabs your personal stuff. Imagine a digital burglar sneaking into your virtual house and snooping around.
Why's it a big deal? Well, because it can lead to some serious trouble. Think identity theft, financial losses, and a whole bunch of headaches you don't want. That's why we need to act fast when we notice something might be off.
Identifying Compromised Email Addresses
Okay, here's where things get interesting. The first thing we need to do is find out if our email address has been compromised and in what data breaches. There are these nifty tools out there, like HaveIBeenPwned.com, that can do some detective work for you. They'll help you figure out if your email addresses have been caught in a data breach. Don't worry too much about what the word "pwned" means; just know that it was a funny typo and was meant to say "owned." Nerds everywhere started using it because, well, we're nerds and it's funny.
Also, please note that when I use the word 'credentials,' I am referring to your username and password. However, in the context of a data breach, I may also be talking about your home address, phone number, and any other personal information that was compromised in the breach.
Take Immediate Action
If you find that your email has not been compromised, you don't need to take any further action. However, I would recommend changing your password often. I update my passwords every few months. I know that might seem like a lot, but what's worse: changing your passwords or losing your life savings?
Once you confirm that your data has been compromised, it's time to take action:
Identify the accounts you use with that email address and check if any of them share the same password. Go to haveibeenpowned.com and enter an email address. If that email and password have been compromised, you will see the bottom of the site turn RED and say "Oh no - pwned!".
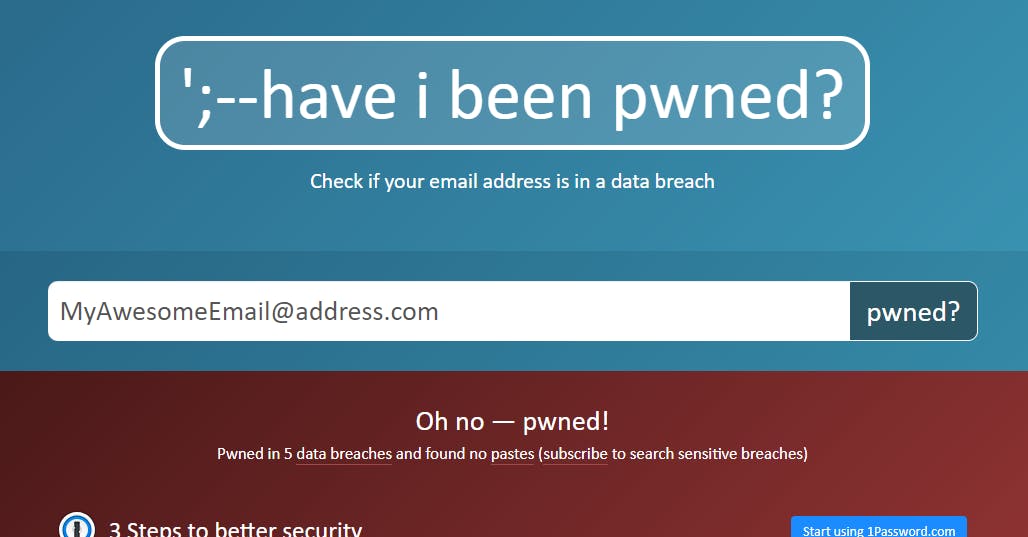
You can scroll down to see which data breaches your email address was involved with.
For Example:
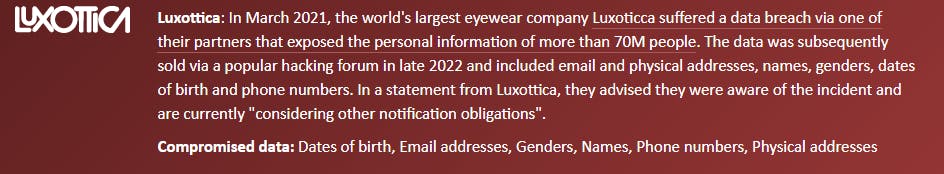
You can see that Luxottica reported a data breach in March of 2001. It involved: Dates of birth, email addresses, genders, names, phone numbers, and physical addresses.
Change the passwords for EVERY site that uses the compromised password. I strongly advise against reusing the same password for every site. Instead, use unique passwords to prevent similar issues in the future. If you're concerned about keeping track of them all, consider using a password manager like 1password.com. Make sure to use a strong master password that you can write down and store in a secure location—preferably an actual safe if you have one.
Set up two-factor or multi-factor authentication. Basic two-factor authentication might involve using a text message with a code to verify that it's you attempting to access your accounts. This added layer of security can significantly enhance the protection of your accounts, even if someone gains access to your password.
Multi-factor authentication (MFA) can employ various forms of authentication and provide alternatives if you lose your phone and can't use it for authentication. I've personally used Microsoft Authentication (available as an app for both Apple and Android) or Google Authenticator (also compatible with both Apple and Android).
Good old-fashioned advice
Having a tough password and 2FA/MFA is a good foundation but oversharing on social media can be a good way to give hackers more information that can potentially lead to gaining access to your data. Those harmless posts about your dog's birthday or your favorite pizza place can be gold mines for cyber crooks looking for personal info.
Be cautious when opening emails. Don't fall for those sneaky phishing emails. Always double-check email senders and avoid clicking on suspicious links. If possible don’t follow links sent to you by email unless you requested the information.
One more thing to help keep your systems safe, don't forget to keep your software and antivirus programs updated. Updates and patches often have fixes for potential pathways for hackers to use to get into systems.
I always emphasize the importance of being aware of your surroundings because it can make a huge difference in staying safe. This principle applies just as much to the online world. You've got to be vigilant in your virtual space, making sure you don't fall into the trap of taking the easy path. Regularly check your accounts, refresh your passwords, and consider using 2FA or MFA to add that extra layer of protection. Oh, and when it comes to passwords, don't forget to change them frequently. If you find it challenging to keep track, think about using a trusted password manager. So, remember: stay vigilant, stay curious, and, above all, stay secure.
Now, here's your call to action. Don't just sit there; take action to secure those compromised accounts. Share your own experiences and tips in the comments below so we can all learn together. And let's work together to make the internet a safer place—spread the word by sharing this article on your social media profiles. Together, we'll lock those digital doors and protect ourselves from unauthorized access!
More Links
Have I Been Pwned (HIBP) | haveibeenpwned.com
Email Encryption Services | protonmail.com
Dark Web Monitoring Services | https://www.experian.com/free-dark-web-email-scan/
Online Security Blogs and Resources | krebsonsecurity.com
Password Policies and Guidelines | pages.nist.gov/800-63-3
Key Definitions:
Data Breach: A data breach is an unauthorized access, disclosure, or acquisition of sensitive information. It occurs when cybercriminals gain access to a system or database containing personal or confidential data, potentially leading to identity theft, financial losses, or other security risks.
Credentials: Credentials refer to the login information used to access online accounts. They typically include a username or email address and a password.
2FA (Two-Factor Authentication): Two-factor authentication is an additional layer of security for online accounts. It requires users to provide two forms of verification before gaining access, often combining something they know (e.g., a password) with something they have (e.g., a mobile device).
MFA (Multi-Factor Authentication): Multi-factor authentication is an advanced security method that involves using multiple forms of verification, such as something you know, something you have, and something you are (biometrics). MFA provides enhanced protection against unauthorized access.
Password Manager: A password manager is a tool or application that helps users securely store, generate, and manage passwords. It can create strong, unique passwords for each online account and store them in an encrypted vault.

